Information Security Policies and Management
IS Management
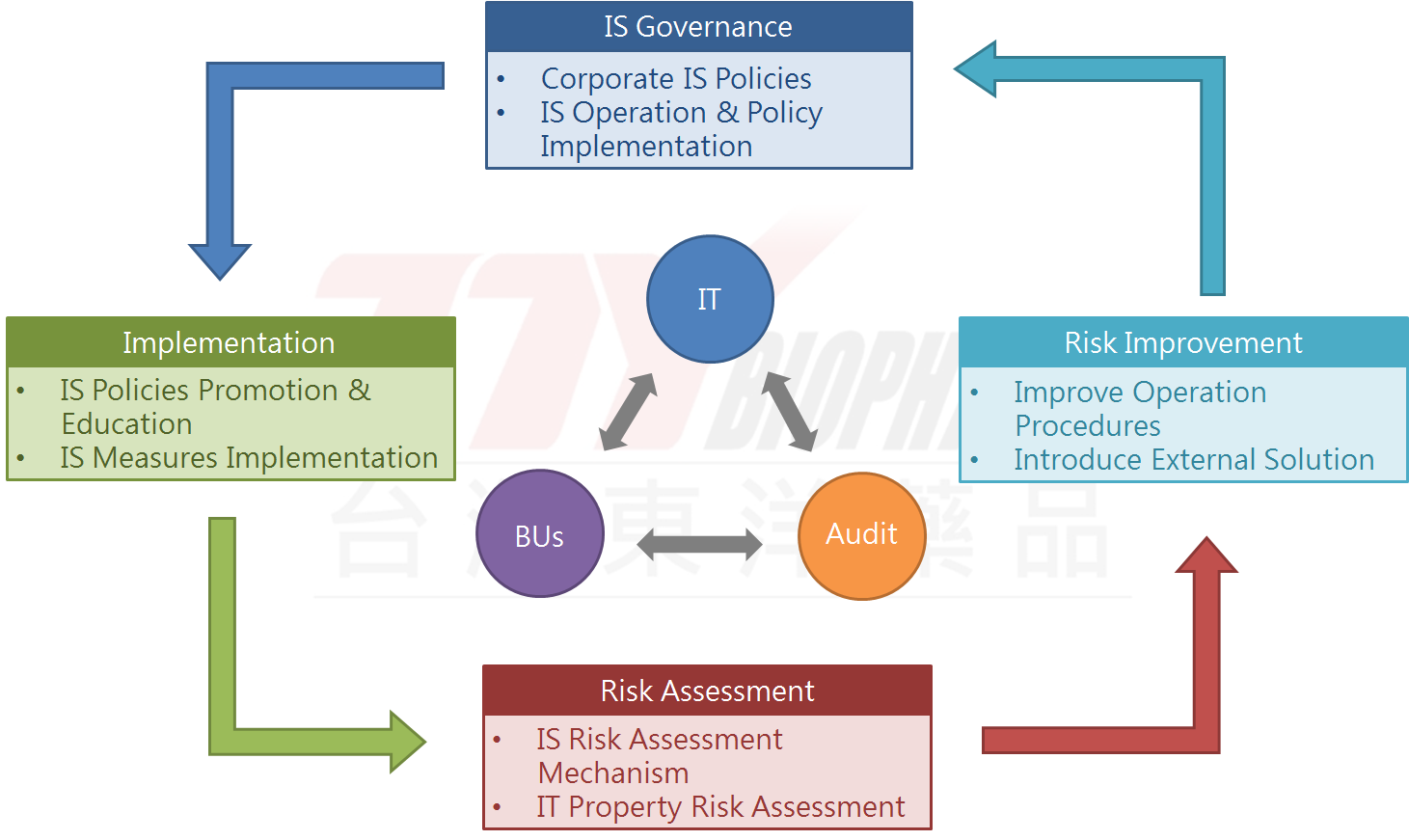
Information Security & Risk Management Framework
- One supervisor and several professional members of Information Technology are in charge of the overall information security and the safe management of information assets. This scope ranges from information security policies and procedures established, to information security operation and policy implementation, to the Company information security governance overview reporting to the BoD. The last report date is on November 6, 2025.
- The auditing manager and dedicated auditor in Auditing supervise and conduct audits of information security affairs. Immediate requests for improvement and action plans will be made if any shortcomings are found. Corrections are regularly followed to mitigate internal information risks.
- The PDCA (Plan-Do-Check-Act) operation mode is adopted to ensure the achievement of reliability targets and continuous improvement.
Information Security Policies and Management
The information security management mechanism includes the following:
1. System specification: formulate the IS management system and standardize personnel operations.
2. Technology application: build IS management equipment and implement IS management measures.
3. Personnel training: conduct IS education and training to enhance the awareness of IS of all colleagues.
1. System specification: formulate the IS management system and standardize personnel operations.
2. Technology application: build IS management equipment and implement IS management measures.
3. Personnel training: conduct IS education and training to enhance the awareness of IS of all colleagues.
Information Security Measures
- TTY conducts regularly reviews on internal information security regulations, and report to the Audit Committee. Based on system standardize, technology application, personnel training to conduct the implementation. The company also complies with the ISO 27005 Risk Assessment Principles, analyzes the internal risk level based on asset value, weakness, threat and impact, and uses the risk assessment results to formulate security measures to improve and enhance the overall information security environment.
- Technology application to prevent the information security threats by establishing relevant IT Preventive System to improve the environmental security. To ensure the operating behavior of the internal staffs are followed the Company's regulation, the implementations are as follows: external threats, permission management, access control and system availability.
- TTY regularly implements information security education and training for new employees quarterly, and several online E-Learning courses to enhance the information security knowledge and professional skills of internal employees. All new employees trained in 2024 were 100% completed the online courses.
Investment in information security management
In the post-epidemic era, global companies are still being attacked by hackers with different intrusion methods. TTY will carry out overall planning from six important directions including: equipment security, external connection access, Internal network control, professional information security testing, implement preventive drills, and personnel information security awareness.
The 2025 implementation includes system and firewall replacement and updates, vulnerability scanning and cybersecurity drills, off-site backup and restore drills, information security training and policy management updates, and reported to the Sustainability Committee and the Board of Directors on November 6, 2025.
In the post-epidemic era, global companies are still being attacked by hackers with different intrusion methods. TTY will carry out overall planning from six important directions including: equipment security, external connection access, Internal network control, professional information security testing, implement preventive drills, and personnel information security awareness.
The 2025 implementation includes system and firewall replacement and updates, vulnerability scanning and cybersecurity drills, off-site backup and restore drills, information security training and policy management updates, and reported to the Sustainability Committee and the Board of Directors on November 6, 2025.